Events
Tackling WordPress security with passQi
By David Eyes
passQi Founder
Special to Santa Cruz Tech Beat
April 14, 2016 — Santa Cruz, CA
[Editor’s note: Santa Cruz Tech Beat has published a variety of articles about passQi in the past. (1, 2, 3, 4, 5). My personal favorite — and an a favorite of SCTB readers — is “Better Than Summer Camp” by passQi 2015 summer intern, Ethan Elshyeb, then aged 14.]
passQi mFactor WordPress plugin now available
Go get it: https://wordpress.org/plugins/passqi-mfactor/. And, keep reading for the whole story.
The enemy of security
From one point of view, passwords can, ironically, seem like the enemy of security for both consumers and site administrators. Simple vs Complex. Unique vs. the same for multiple sites. Brute force vulnerability. Social engineering. Headaches, and ones which WordPress sites, in particular, need to be concerned with simply due to its ubiquity as an easily identified target. Its vulnerabilities quickly become generally known among those who would exploit sites with less than rigorous site security.
News of security breaches continues along unabated, while the question of device security captures the headlines. It’s easy to slip in to overwhelm, or “hasn’t happened to me yet” passivity. But obviously, the time to think about security is before an incident occurs.
One of the obstacles to action is that the most obvious answer for password or login security, some form of two-factor authentication, has been by and large an awkward and cumbersome experience to date. It is a bolt-on to the existing password login mechanism and requires a separate procedure and a second challenge to accomplish. Modeled on twenty year old key fob technology, today’s two-factor typically requires a stand-alone app to serve up to the user the one time codes that need to be typed in in along with one’s username and password. And activation of typical TOTP or “Google Authenticator” type two-factor requires more than a little motivation to get over the technical and procedural hurdle of registering the “shared secret” needed for the technology to work.
Isn’t there an easier way?
Isn’t there an easier way, without a complete “rip and replace” of the whole idea of passwords? Shouldn’t we be able to use the ubiquitous smartphone, with all of its power, to provide a super-secure mechanism for declaring our identity without requiring yet another device to carry around or an arcane series of manual steps? Can’t sites maintain the baseline of username password features while adding easy opt-in for their users to add two factor protection?
Enter passQi
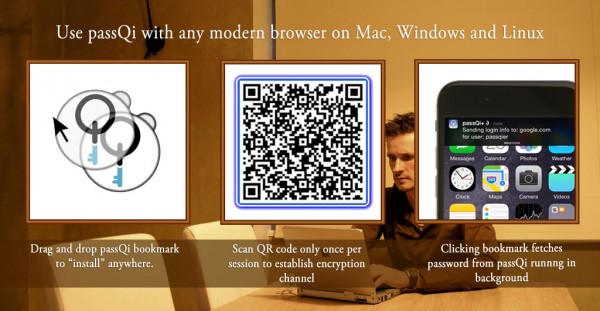
Enter passQi. We have enhanced the user account security experience, first by making password login simple and automated, without requiring that you store passwords in the cloud. The passQi smartphone app makes your phone the master of your identity, and through its secure bridging technology, allows users to automate login on any available computer with a simple drag and drop helper bookmark lightweight “install”. By scanning a QR code at the start of a session, the user’s phone becomes “bridged” to the target browser, and passwords are encrypted with a one-time AES encryption key each time a user wants to log in to a site.
passQi mFactor technology is available as an easy to install WordPress plugin
The gold standard for account security however remains two-factor authentication, and passQi’s secure bridging, by providing a secure link between the phone and the device, makes it possible to easily add a second channel or pathway for authentication (login) that uniquely demonstrates the possession of the phone by the user at the time of logging in in a way that is almost completely transparent to the user. In other words, provides two-factor authentication for sites which deploy the passQi mFactor technology – available now as an easy to install plugin for WordPress.
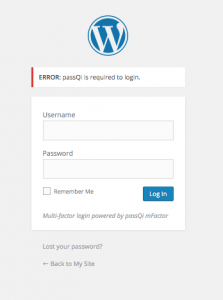
If the username and password are correctly entered but the passQi app was not used, hackers will see this message. (Contributed)
The passQi 2 password app automatically provides each account with a secondary and secret soft token, one which is unknown even to the user and is essentially impossible to guess or discover by brute force. By encrypting this token in the cloud as part of the password relay process, it can be pushed as a cookie to the target site every time the user has passQi automate entry of their username and password on a login page.
A passQi mFactor aware site – such as one with the new WordPress plugin installed – can decrypt the token and determine that the username and password, as well as of course the token, must have been relayed using passQi – and that therefore, the user must have been present with their smartphone. Simple entering the username and password is not enough, for users (or administrators setting policy for their users) who simply check the “require passQi to Login” box in their profiles – that’s it.
Of course, the most important security measure that administrators should take with WordPress is to ensure that their systems are kept constantly up to date. As an open source project, vulnerabilities are readily discovered – and also quickly fixed. Of almost equal importance is to make sure that your account logins are as secure as possible – an exploit usually is made through some compromised account gaining privilege.
passQi mFactor requires that users have the passQi app – currently available in the iPhone app store, and also available in beta for Android (see https://www.passqi.com/android-beta/). passQi 2 for iPhone was recently updated with Apple Watch support. It provides management for all of your site passwords without storing them in the cloud and also support for TOTP style two-step verification as an in-app purchase.
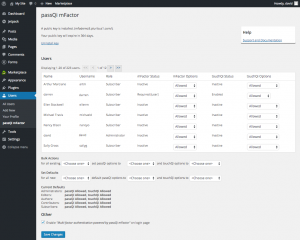
Administrator configuration options for passQi mFactor plugin for WordPress gives fine grain control of user two-factor settings. (Contributed)
Administrators can configure use of mFactor on a per-account or per-role basis, requiring, denying orallowing passQi to be used for each user. With the default “allow” setting, it is up to individual users to opt-in to passQi mFactor by simply clicking a checkbox in their profile. If their device supports biometric authentication (eg, Touch ID on the iPhone), this can also be added as a further required step: users will be prompted to perform Touch Authentication every time they log in.
Installation of passQi mFactor requires site admins obtain a subscription form the passQi store. Both commercial and free non-commercial subscriptions are available.
passQi mFactor and the passsQi app work together to transform user login into a more simple to manage and more secure technology.
Learn more about passQi mFactor’s unique technology by downloading our white paper here: https://www.passqi.com/download-passqi-whitepaper/
###
If you wish to republish this article, please follow our Terms of Use.
###
Tagged passQi, password security