Companies
Another Breach at a Major Password Manager Site: Why passQi is Different

By David Eyes
CEO passQi, Inc.
June 18, 2015 — Santa Cruz, CA
Disclaimer: there is NO such thing as “absolute security” — it is always a question of degree.
LastPass issued a security advisory reporting untoward activity on their network and advising users that those with weak passwords (especially) were at risk and should change their passwords.
This is at least the second time that LastPass has had such an exposure. And here’s why it is likely to be a risk for them and other providers who store encrypted passwords in the cloud, and how a solution like passQi avoids this type of risk.
The short answer is, there are simply some things that are bad to put in a centralized, network accessible place. Especially if the ultimate barrier between your passwords and disclosure of all of your passwords is a single password which can itself be of limited complexity.
By storing all of the passwords in one location, the cost/payoff for a hacker to invest in breaching the network security of the target is high, because once in, they will have access to essentially all (encrypted) password vaults. If these can be captured, they can then be subject to offline cracking, especially if there is a “weakest link” in the security model – simple user passwords.
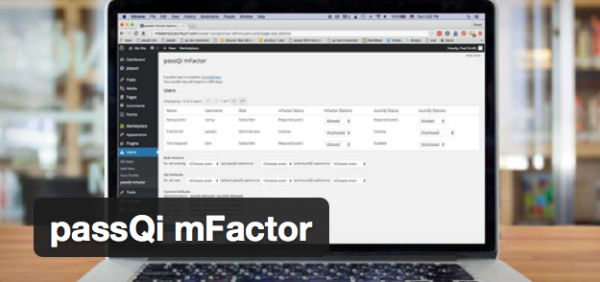
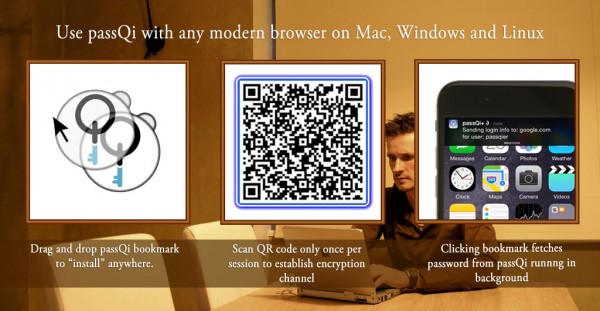
passQi takes a completely different approach, and though it relays encrypted password payloads through the cloud, it doesn’t store any passwords there – they are stored in each individual user’s own phone, where they are both encrypted in storage, and, most uniquely, encrypted in transit with a one-time AES (Advanced Encryption Standard) key which is known only to the target web page and the phone itself.
When a passQi bridge session is initiated, the user scans a QR code generated by the passQi bookmark, which contains a session identifier (for the bridge session) and an AES key, which is also generated in the browser itself. The session identifier enables the bookmark code to carry on a dialog with the passQi cloud, waiting for a user response; the passQi app also uses this session identifier to relay the password encrypted with the AES key.
Subsequent requests through the passQi bookmark are relayed automatically, without requiring another QR scan.
The three key distinctions which make the passQi design safer are:
Continue reading article here: https://www.passqi.com/another-cloud-centric-solution-breach/
###
Tagged passQi, password security